
Nessus professional is nice for small business vulnerability management, but the reporting is lacking until you upgrade to Security Center. VulnWhisperer uses the elastic stack to provide scan result summaries that are easy to review and report to management or operations teams for remediation. Impress your C-suite with vulnerability reports using VulnWhisperer.
Prerequisites:
- Ubuntu 18 minimum installation
- Accessible Nessus instance
Recommended Resources:
- CPU 2
- Memory 8GB
- Storage 40GB
I am using an Ubuntu minimum installation virtual machine within VMware ESXI for vulnwhisperer and a separate virtual machine within VMware ESXI with Nessus installed.
Lets start by kicking off an update.
trenchesofit@vulnwhisperer:~$ sudo apt-get updateDocker Installation
Add a few required packages.
trenchesofit@vulnwhisperer:~$ sudo apt-get install software-properties-common ca-certificates apt-transport-httpsInstall Docker signed packages.
trenchesofit@vulnwhisperer:~$ sudo curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add -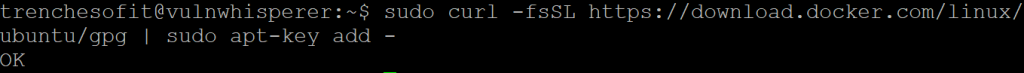
Add Docker repositories.
trenchesofit@vulnwhisperer:~$ sudo add-apt-repository \
> "deb [arch=amd64] https://download.docker.com/linux/ubuntu \
> $(lsb_release -cs) \
> stable"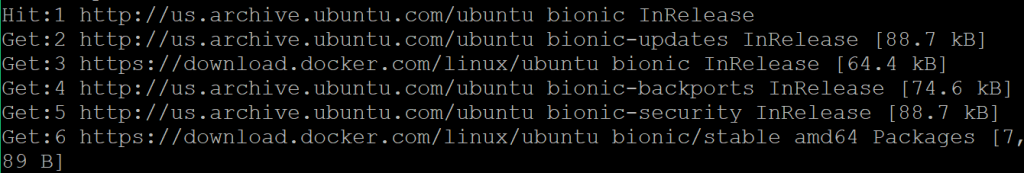
Docker installation.
trenchesofit@vulnwhisperer:~$ sudo apt-get install docker-ceEnable docker.
trenchesofit@vulnwhisperer:~$ sudo systemctl start docker
trenchesofit@vulnwhisperer:~$ sudo systemctl enable docker
Synchronizing state of docker.service with SysV service script with /lib/systemd/systemd-sysv-install.
Executing: /lib/systemd/systemd-sysv-install enable dockerLets check the status of the service to ensure all is well.
trenchesofit@vulnwhisperer:~$ systemctl docker status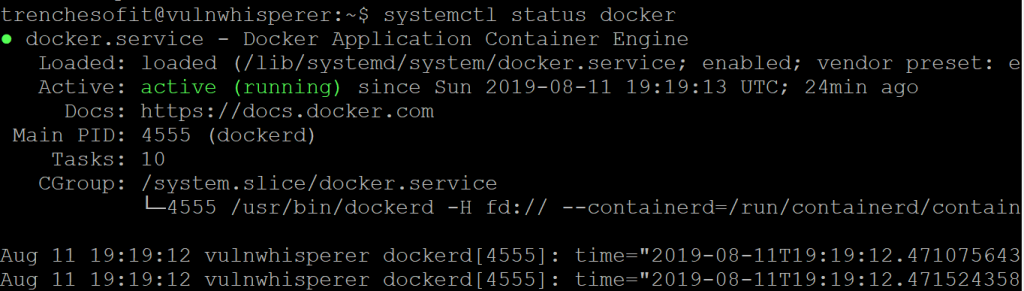
Docker-Compose Installation
Now lets install docker-compose to simplify the VulnWhisperer installation.
trenchesofit@vulnwhisperer:~$ sudo curl -L https://github.com/docker/compose/releases/download/1.25.0-rc2/docker-compose-`uname -s`-`uname -m` -o /usr/local/bin/docker-compose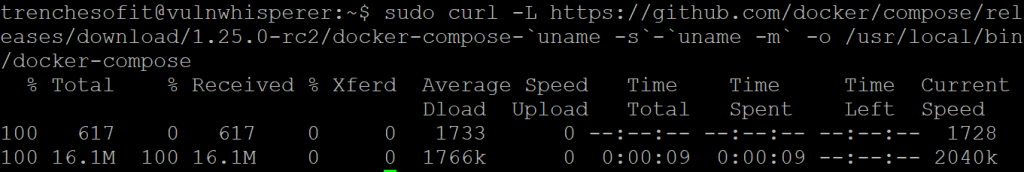
Set execute permissions to the binary.
trenchesofit@vulnwhisperer:~$ sudo chmod +x /usr/local/bin/docker-composeTo ensure the installation was successful, we will check the version installed.
trenchesofit@vulnwhisperer:~$ docker-compose --version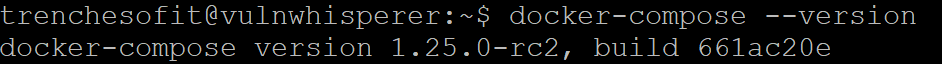
Get the Git Repository
[trenchesofit@VulnWhisperer ~]$ git clone https://github.com/HASecuritySolutions/VulnWhisperer.git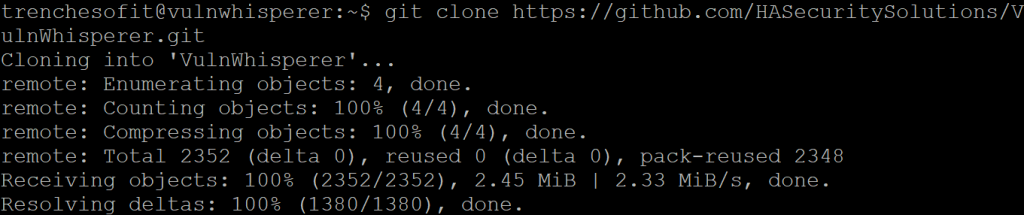
Configure VulnWhisperer
Lets pull the required libraries for Debian based systems.
trenchesofit@vulnwhisperer:~/VulnWhisperer/bin$ sudo apt-get install zlib1g-dev libxml2-dev libxslt1-devEdit the frameworks_example.ini found in the /VulnWhisperer/configs directory. Make the same change within the vulnwhisperer.ini file located in /VulnWhisperer/resources/elk6/
[trenchesofit@localhost configs]$ sudo vi frameworks_example.iniHere you can edit either the access_key and secret_key or the username and password. The default configuration also looks at the local machine to pull the vulnerability scans, so if your scanner is on another server, ensure to enter that IP after hostname.
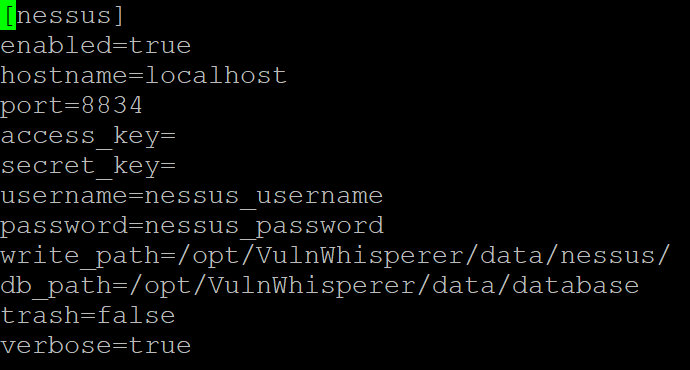
Allow additional permissions to the ./data folder located in the VulnWhisperer directory.
trenchesofit@vulnwhisperer:~/VulnWhisperer/$ sudo chmod -R 666 dataAlso we will have to add additional permissions to the logstash.yml file located in /VulnWhisperer/resources/elk6/logstash.yml
trenchesofit@vulnwhisperer:~/VulnWhisperer/$ chmod 666 docker/logstash.ymlFinally lets kick off the docker-compose command.
trenchesofit@vulnwhisperer:~/VulnWhisperer/$ sudo docker-compose -f docker-compose.v6.yml up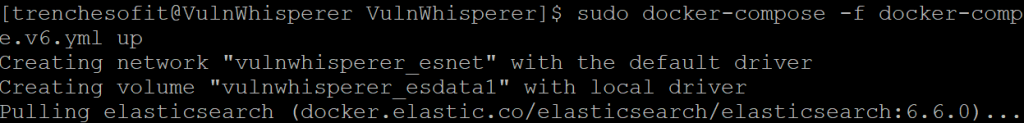
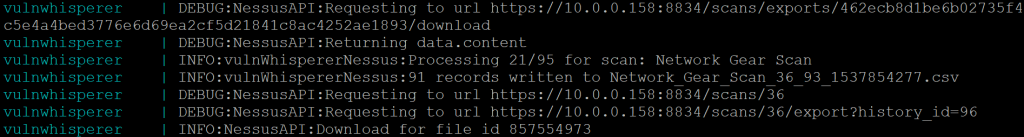
Execute crontab job at set schedule.
[trtrenchesofit@vulnwhisperer:~/VulnWhisperer/$ sudo vi /etc/crontab
Add the following line.
0 8 * * * /usr/bin/docker-compose up vulnwhisp-vulnwhispererNavigate to http://VULNWHISPERER_IP:5601
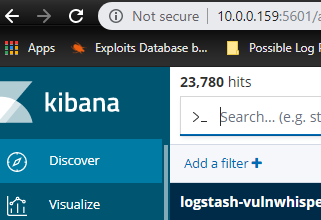
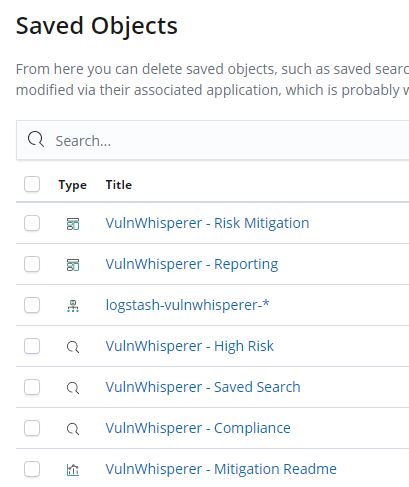
In the left pane click Management > Saved Objects > Import > VulnWhisperer/resources/elk6/kibana.json. After importing the file you will see 27 new objects.
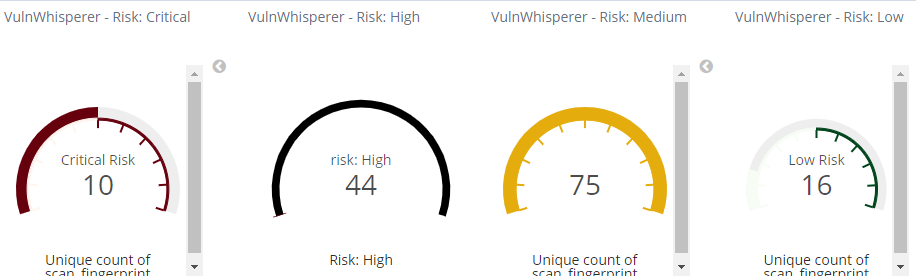
Last navigate to the Dashboard and analyze the collected vulnerability data.
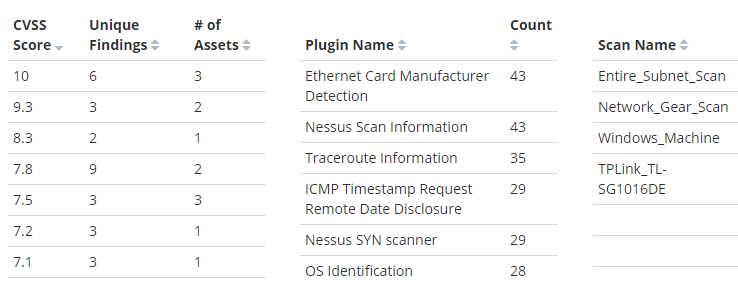
That’s all there is to it! VulnWhisperer is a great framework for vulnerability management analysis and reporting. Please reach out in the here if you have any issues with the install or configuration. Until next time “Stay safe in the Trenches of IT!”